here more info on this topic
http://log.nadim.cc/?p=78
Update: According to Microsoft, SmartScreen sends a hash of the app installer and its digital signature, if any. A combination of the hash and the user’s IP address is still enough to identify that IP address x attempted to install software y.
Update 2: Another researcher has discovered that a filename of the app you’re trying to install is indeed sent to Microsoft. This severely strengthens privacy concerns.
Update 3: Approximately 14 hours after this article was published, another scan of Microsoft’s SmartScreen servers reveals that they have been reconfigured to no longer support SSLv2. The servers now only support SSLv3 connections.
I’ve recently been using the final, Released to Manufacturing version of Windows 8 on one of my computers, to much delight. I’ve been very impressed by how fast, well-designed, functional and capable this latest iteration of Windows is. However, my tinkering around from a security/privacy perspective has left me concerned.
Windows 8 has a new featured called Windows SmartScreen, which is turned on by default. Windows SmartScreen’s purpose is to “screen” every single application you try to install from the Internet in order to inform you whether it’s safe to proceed with installing it or not. Here’s how SmartScreen works:
You download any application from the Internet. Say, the Tor Browser Bundle.
You open the installer. Windows SmartScreen gathers some identifying information about your application, and sends the data to Microsoft.
If Microsoft replies saying that the application is not signed with a proper certificate, the user gets an error that looks something like this.
There are a few serious problems here. The big problem is that Windows 8 is configured to immediately tell Microsoft about every app you download and install. This is a very serious privacy problem, specifically because Microsoft is the central point of authority and data collection/retention here and therefore becomes vulnerable to being served judicial subpoenas or National Security Letters intended to monitor targeted users. This situation is exacerbated when Windows 8 is deployed in countries experiencing political turmoil or repressive political situations.
This problem can however get even more serious: It may be possible to intercept SmartScreen’s communications to Microsoft and thus learn about every single application downloaded and installed by a target. Here is my analysis:
A quick packet capture showed the following activity happening immediately when I tried to install the Tor Browser Bundle:
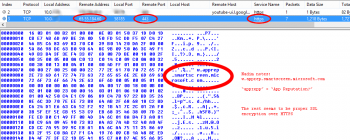
SmartScreen appeared to connect over HTTPS to a server in Redmond (apprep.smartscreen.microsoft.com, 65.55.184.60, run by Microsoft) in order to communicate information about the application I was trying to install.
After running some tests on this Microsoft server, I discovered that it ran Microsoft IIS 7.5 to handle its HTTPS connections. The Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception. The SSL Certificate Authority chain goes down from “GTE CyberTrust Global Root” to “Microsoft Secure Server Authority.” The Certificate Authority model is itself susceptible to some serious problems.
I haven’t checked whether Windows SmartScreen does in fact use SSLv2, but the fact that the Microsoft servers support it is concerning. Furthermore, SmartScreen is not easy to disable, and Windows will periodically warn users to re-enable it should they attempt to disable it.
To recap, here are the concerns posed by SmartScreen in Windows 8:
Windows 8 will, by default, inform Microsoft of every app downloaded and installed by every user. This puts Microsoft in a compromising, omniscient situation where they are capable of retaining information on the application usage of all Windows 8 users, thus posing a serious privacy concern. The user is not informed of this while installing and setting up Windows 8, even though they are given the option to disable SmartScreen (which is enabled by default.)
Windows 8 appears to send this information to Microsoft to a server that relies on Certificate Authorities for authentication and supports an outdated and insecure method of encrypted communication. It is possible that these insecurities could allow a malicious third party to target a Windows 8 user and learn which applications they are using. This allows them to profile the user and decide how to best exploit their personal selection of applications and their computing habits.
I find Microsoft’s decision to design SmartScreen in such a privacy-free fashion to be a very bad choice, and I really hope that these concerns regarding SmartScreen will be addressed in near-future updates.



